10 most common forms of DeFi attacks and how to prevent them

When the market goes into downtrend, scams, attacks and rug pulls emerge and become more common. Therefore, it is crucial that investors equip themselves with knowledge to protect their funds and assets, especially during this time.
Below is a list of 10 prominent forms of DeFi attacks today. Among these, there are a few sophisticated forms of attacks that many users do not know. In addition, Coin98 Insights also has an article on 19 common scams in crypto, including a set of basic tricks often used by hackers.
10 common forms of DeFi attacks
Oracle attack
Oracle is a system that provides pricing information for asset classes, and DeFi projects rely heavily on oracle for price updates. If the price of token A in the market is $10, but in a DeFi protocol, it shows $100, users would definitely buy this token in the market and sell on that protocol to make huge profits. This damages not only the protocol, but also those who have provided assets into that protocol.
Solution: To avoid encountering these situations and causing unnecessary damage, users should use DeFi protocols that integrate reputable oracles. This will greatly reduce the risks of oracle attacks in general.
Flash loan attack
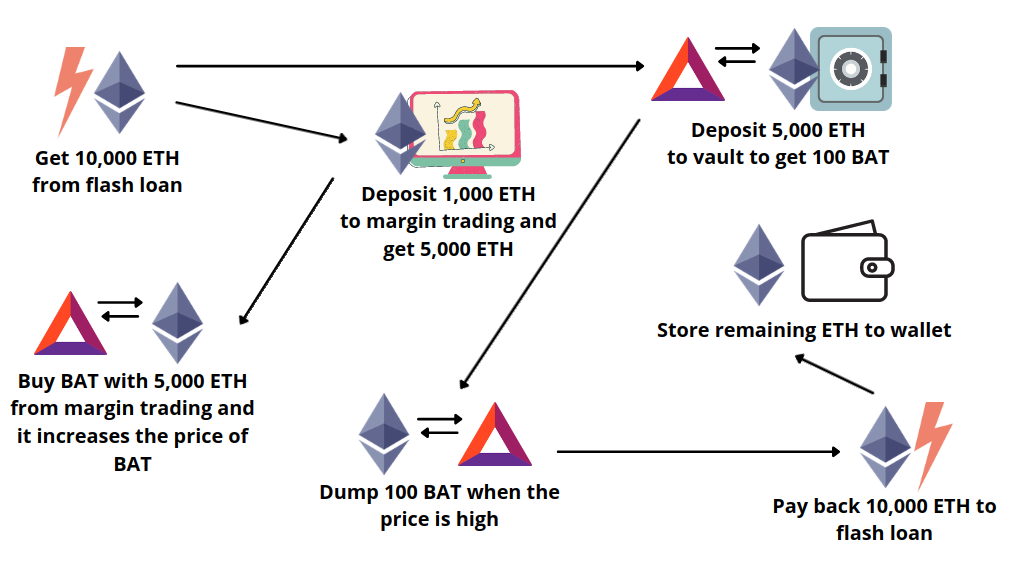
Flash loans are uncollateralized loans under one condition: the loan must be repaid to the lending platform in the same transaction. In other words, the borrower can do whatever with that loan, then pay back the borrowed amount, all of which happens in 1 transaction.
Nearly all flash loan attacks are programmed and executed by bots. Therefore, the attackers can even profit while sleeping, and DeFi protocols with price differences (usually due to oracle errors) are usually the victims.
Taking the Oracle attack example above, if a user sees an opportunity in the price difference of token A, $10 and $100, but they only have token B instead of money, what will they do?
⇒ They’ll use token B as collateral to borrow token A, ETH, USDC, etc. to buy token A, then sell on the DeFi protocol with oracle error, then repay and get token B back.
However, this is only a simplified example. Flash loan attacks can take many different forms and are much more complex in reality. To get a deeper understanding about flash loan attacks, visit this link.
Solution: Most flash loan attacks occur due to oracle error or unbalanced asset ratio in liquidity pools. Therefore, it is recommended to use protocols with reputable oracles and high trading volume. A high number of users means that when a minor price difference happens, there will always be arbitrage traders balancing the pooled asset ratio.
51% attack
If an attacker possesses a large amount of governance tokens, they can take advantage of the protocol's governance mechanism and profit themselves. This is known as a 51% attack and can be combined with flash loans to create an attack without the need to own the project's tokens.
For example, a DeFi protocol has a governance mechanism that only requires more than 50% of voted token A to agree with a proposal for it to be approved. In this case, the attacker may use flash loans and borrow 51% of token A (or borrow money to buy token A), then create and approve a proposal to send 100 million USDC to himself. In the end, he only needs to pay the debt with a small fee and pocket a profit of 100 million USDC.
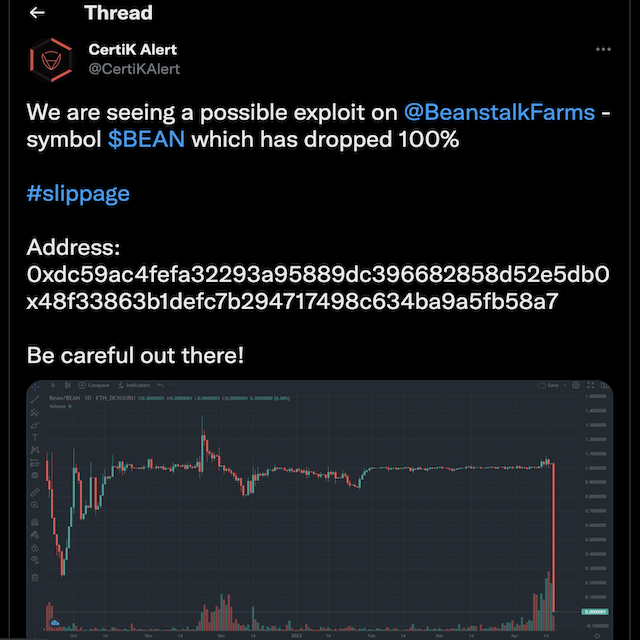
This case once happened to Beanstalk and the attackers pocketed 182 million USDC.
Solution: To avoid projects with risks of 51% attacks, users should choose DeFi protocols with tight governance mechanisms or have large barriers to attackers.
For example, investors can consider projects that require a high consensus rate, or require owning great asset value in the portfolio before owning enough governance tokens for proposals to be approved.
Front-running attack
Front-running is when an attacker knows a future transaction will affect the price and places an order right before that transaction to make profit. The design of Ethereum and other similar blockchains has created opportunities for bots to profit by front-running other transactions.
For example, with the USDC-SAK3 trading pair:
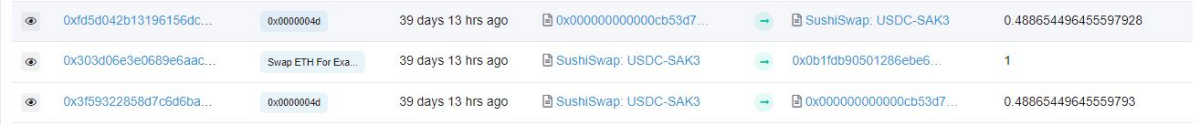
It can easily be seen that right before and after the buy order of 1 SAK3, there are 2 buy and sell orders of 0.48 SAK3 made by the same address. This is a typical example of users being front-runned in crypto. As seen in the transaction hashes above, in just two transactions, this bot has gained more than $1,500 by buying SAK3 at $7,473 and selling at $9,013.
Solution: To prevent front-running, investors can:
- Split into multiple transactions.
- Set low slippage rates.
Admin key attack
Some protocols have the “admin key”, allowing a special address to have full control over the protocol’s funds. If the admin key gets attacked, the funds might be stolen.
A typical example is the EasyFi attack, where the CEO’s admin key got attacked and $6 million was stolen from its liquidity pool, along with 2.98 million EASY tokens (valued at $75 million at the time).
Solution: Investors need to choose protocols carefully, and never put all funds into projects with little to no team or backer information. In addition, thorough consideration must be made to protocols with admin keys, where too much power is given to a person or certain group.
Front-end attack
Front-ends are the display interface of applications, which when interacted with, affects the underlying elements (back-ends) to help users perform different actions. This part of the interface can also be hacked and cause damage to users.
An example is Badger DAO with a $120 million worth of damage at the time. The attacker targeted Badger DAO's API key, causing users’ interactions to grant unlimited approval to the wallets, creating an opportunity for the attacker to withdraw assets from those wallets.
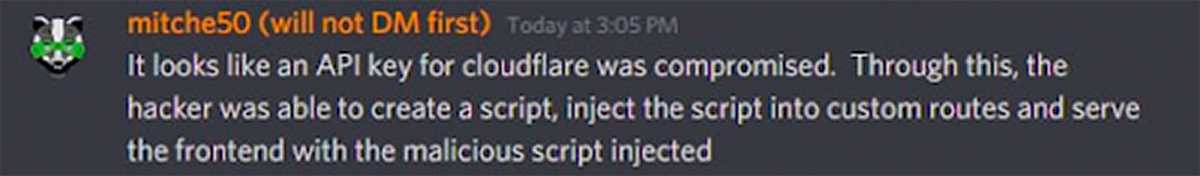
Solution: Always pay attention to approvals when making transactions on wallets. If users have interacted and granted approval to a new project, they can use revoke tools such as the Coin98 Super App or Approved.zone.
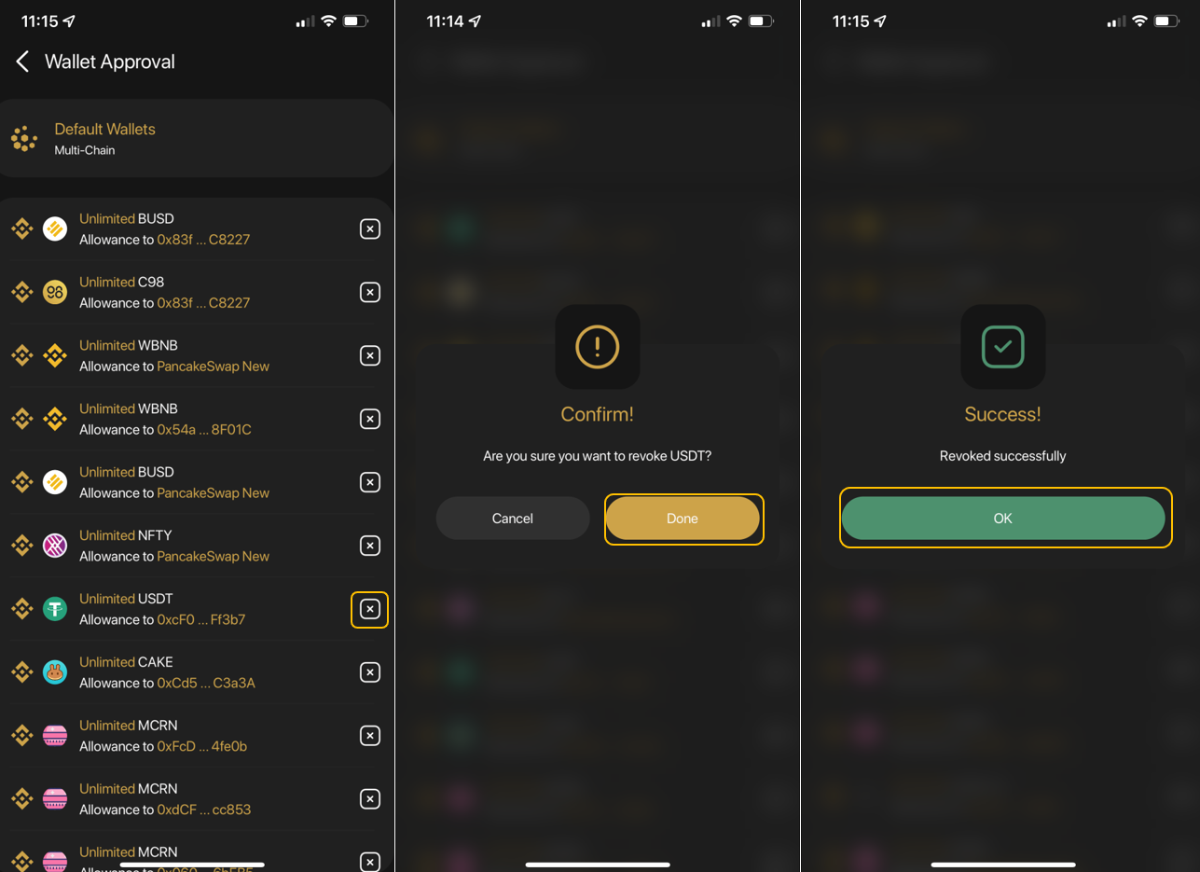
Social Media attack
Having accounts on social media platforms such as Discord, Twitter or Telegram is common for crypto users. Along with the rising needs to gain information, seek opportunities and join big or small communities is the emergence of scammers and hackers. They almost always pose as project team members to lure users into phishing links or websites.
This is an extremely common form of attack and it happens everyday, therefore, users must stay alert to avoid falling for these tricks.
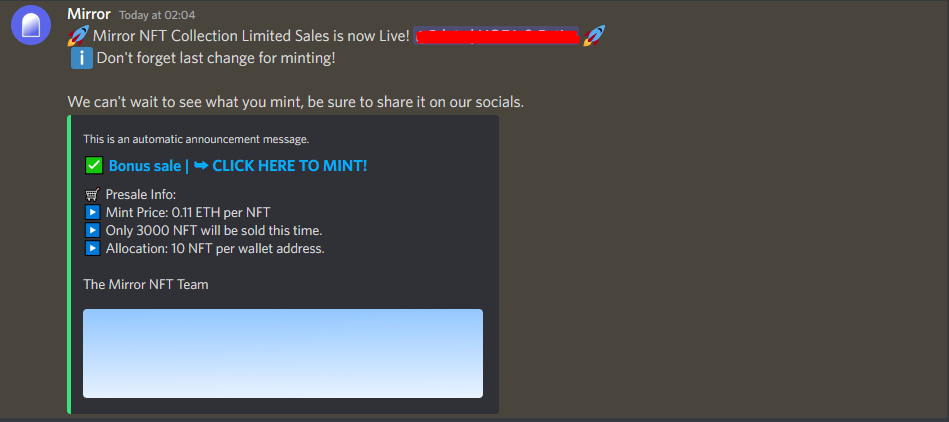
Solution: No matter where users are, if they receive an unbelievably attractive offer anywhere, it is almost always a scam. Although social media attacks are easy to spot, their frequency is increasing and they’re becoming more sophisticated day by day. Users must pay attention to offers involving their funds.
Social Media control attack
This is the more sophisticated form of social media attack, where the attackers hack and take control over the project team’s social media account to distribute wrongful information, stealing users’ funds.
The Instagram account of one of the most popular NFT collections - Bored Ape - was hacked. The attacker then announced an airdrop for Bored Ape holders, which only require holders to connect their wallets. Approximately $2.8 million worth of NFTs was stolen after this incident.

Solution: As mentioned above, nothing is free, so users must be extremely careful when seeing free airdrops, giveaways, etc. even on reputable projects’ social media accounts. It is best to double check with the project’s team before participating in these events.
Layer 1 attack
“The security of smart contracts is only equivalent to the security of the blockchain they run on”. If the blockchain is hacked, all projects built on it will be affected and cause damage to users.
For example, Ethereum Classic, an Ethereum hard fork, suffered a 51% attack and lost the trust of its community.
Solution: Join prestigious layer 1 networks that have been battle tested for a long time.
Attack by other parties
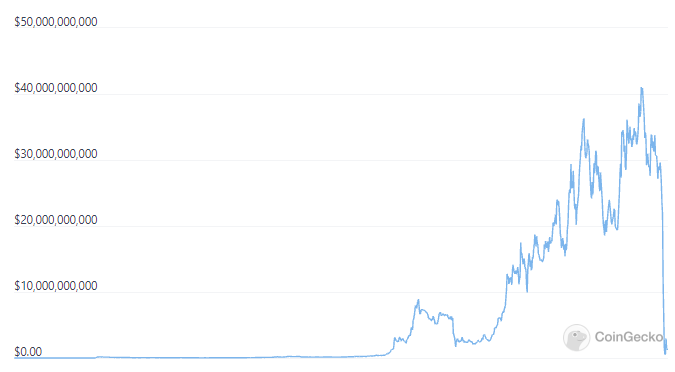
Many people are aware of UST losing its peg, causing the collapse of the Terra empire. The cause of the attack was most likely pre-arranged, since a large amount of UST was withdrawn in Anchor in just a short time, leading to panic sell.
This event went beyond the crypto market as a project once valued at $40 billion collapsed in just a few days. This has shown the riskiness of a market with fledgling capital like crypto, when even the top projects can "disappear" in the blink of an eye.
Solution: Don’t put all eggs in one basket, even if the project is on top of the market. Making money in crypto is not easy and investors should not put too much faith in a certain project alone.
Conclusion
Before making money, learn how to keep it. Even though DeFi experienced a blast throughout 2021, it is still new and therefore contains plenty of risks. As the market goes into downtrend, investors should prioritize protecting assets rather than focusing on high-risk earning opportunities.